Sans 6 Steps Incident Response

The 6 steps in depth incident response helps organizations ensure that organizations know of security incidents and that they can act quickly to minimize damage caused.
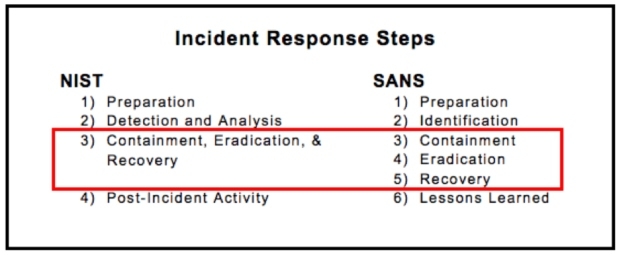
Sans 6 steps incident response. The aim is also to prevent follow on attacks or related incidents from taking place in the future. It s a 6 step framework that you can use to build your specific company plan around. Though more youthful than nist their sole focus is security and they ve become an industry standard framework for incident response. Assemble your team 2.
Detect and ascertain the source 3. What is the purpose of immediately reporting a cybersecurity incident. Incident handling featuring 153 papers as of august 27 2020. It s a good way to describe the sans methodology for incident handling compelled by stephen northcutt and others.
Contain and recover 4. The preparation of the computer incident response team cirt through. It is a 6 steps methodology. The sans incident response process consists of six steps.
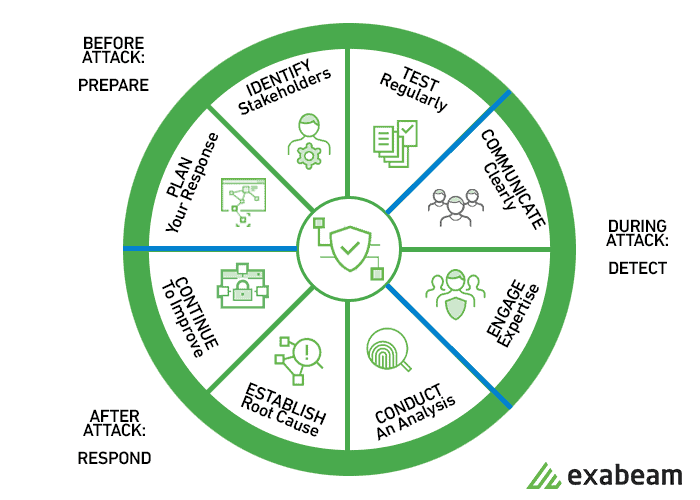
What are the 6 steps to take after a security incident occurs. California and colorado are enacting similar rules in the us and that trend is likely to continue. Join the sans community to receive the latest curated cyber security news vulnerabilities and mitigations training opportunities and our webcast schedule. 12 10 6 implement a process to update and manage the incident response plan per industry and organizational changes how to create an incident response plan an incident response plan should be set up to address a suspected data breach in a series of phases.
Steps that are unanimous among security practitioners. 5239 19 from us navy staff office back in 1996. For this case we ll walk through a typical remote access trojan based incident. The sans ir process focuses on a typical malware based event focused on a single threaded incident and response.
Introduction an incident is a matter of when not if a compromise or violation of an organizat ionõs security will happen. 3 2 4 6 1. With its origins on the computer incident response guidebook pub.